First Steps To Secure Your OCI Account
A Chain Is Only As Secure As Its Weakest Link
Introduction
You've logged into OCI for the first time, and you're super keen to get started with the Always Free services such as Compute and ATP.
Before you go any further - you need to make sure your OCI login is protected OCI comes with built-in functionality to add MFA and controls based on IP addresses.
This is important because any security configuration applied to OCI services can be updated or overridden by anyone with an OCI Administrator account. Security on individual services is only as strong as the security on the master account.
The configuration described applies to the latest version of OCI that manages security using Domains. Older accounts will use IDCS instead but the concepts (network perimeters, Sign-on Policies) are the same.
Important
If add or change login criteria, you need to make sure that you don't lock yourself out. You must verify your sign-on still works using an Incognito window, while keeping your OCI session open. This allows you to revert any changes that you may regret.
If you're adding MFA to an OCI environment that has existing users, remember that signon rule changes apply to all users unless these are configured as specific exceptions. For example, if you are using Oracle Integration Cloud (OIC) and a service account is used to invoke OIC integrations from a third-party system, the third-party system will not be able to use MFA in the same way as an end-user login. This must be catered for in the Sign-on Policies.
Enabling Multi-Factor Authentication (MFA)
Add MFA Factors
Navigate to Identity and Security -> Domains.
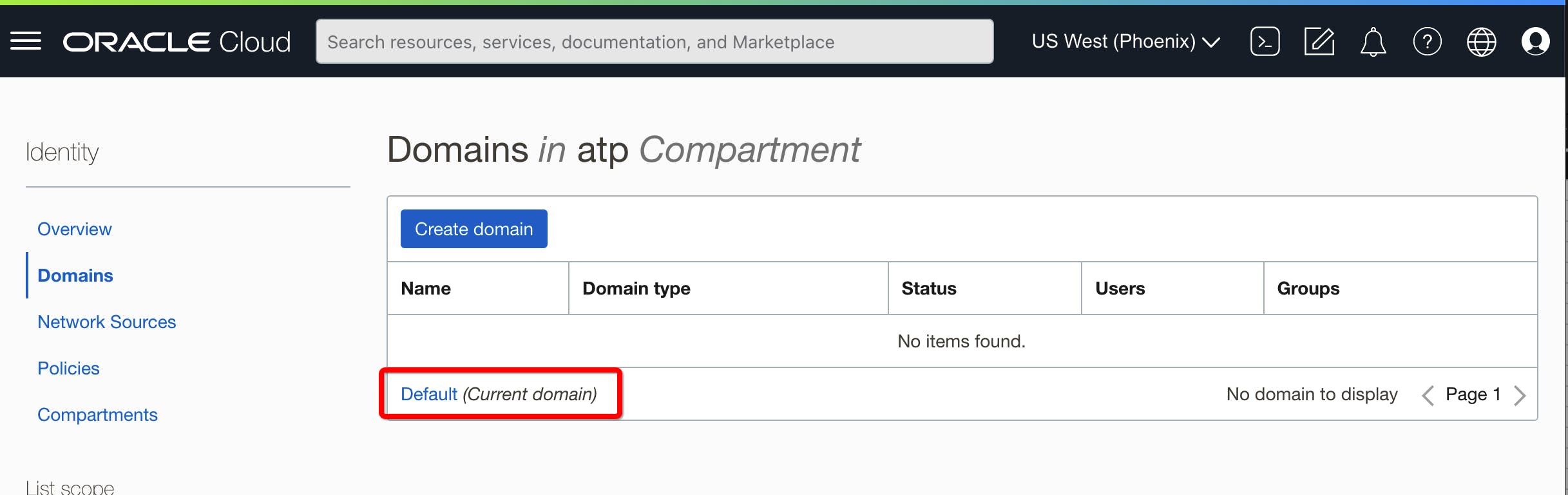
Open the Default domain, then click on the Security option in the menu.
Under MFA, you'll see options to configure factors such as email, mobile app, or phone call. Phone and SMS works with older IDCS-based OCI - for the newer domain-based OCI, you can use these if you have an account with Vonage. My personal preference is to use Oracle's mobile app.
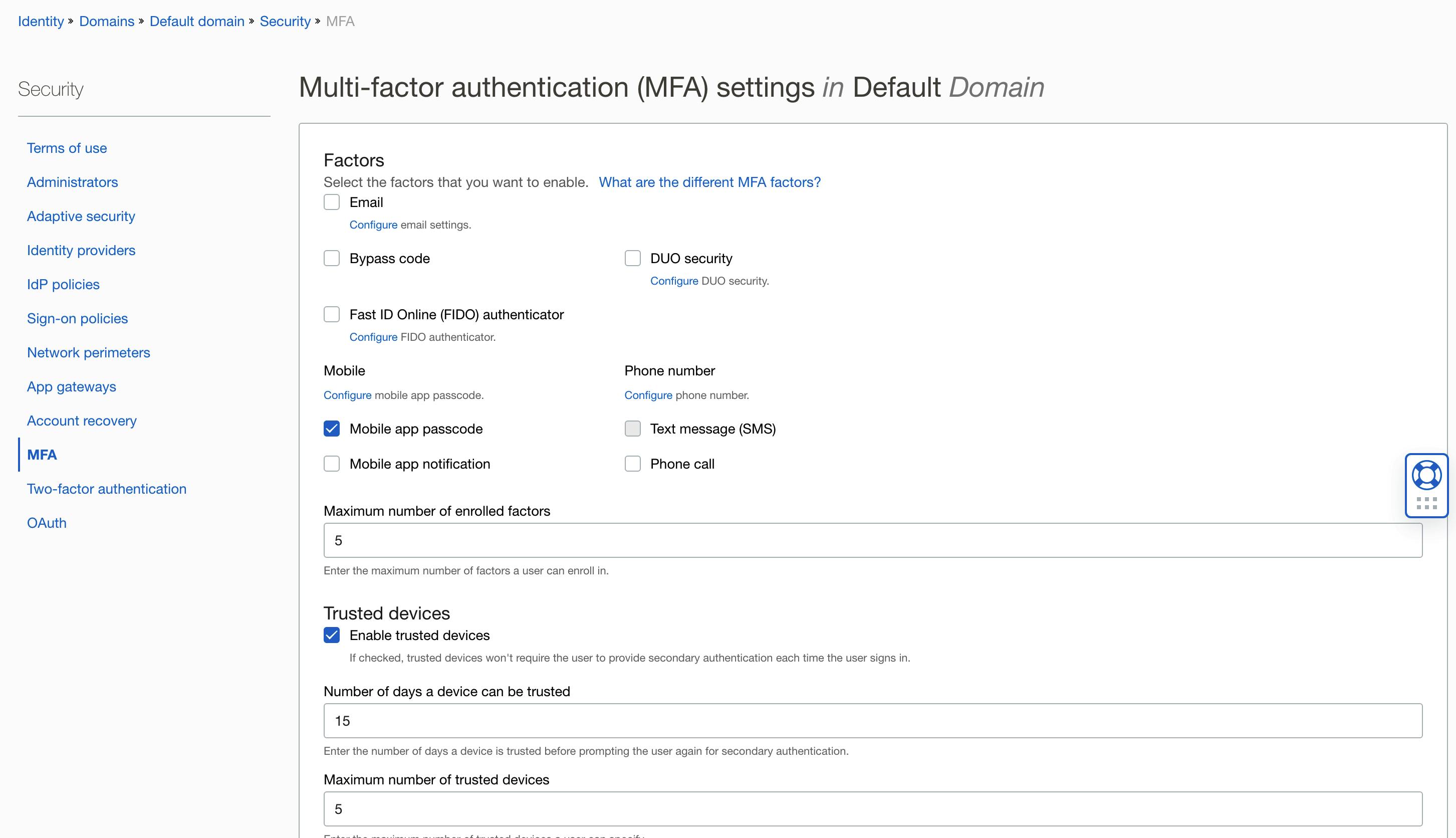
Save your changes. At this point, you have only enabled the factors - they become effective once added to a Sign-on Policy.
Sign-on Policy
Click on Sign-on Policies
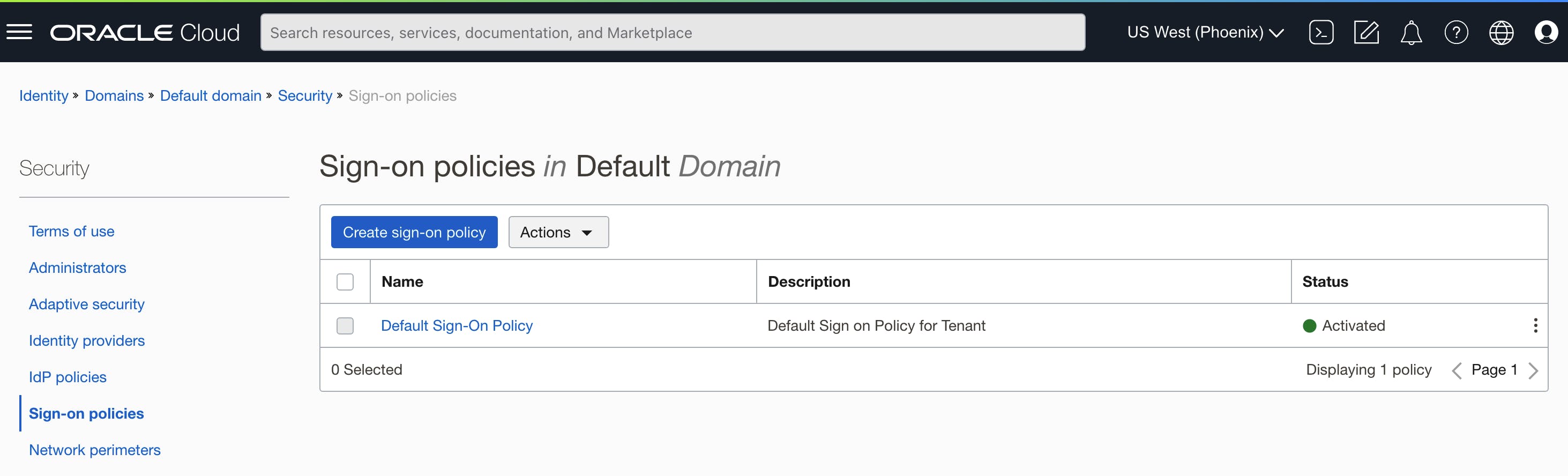
Edit the Default Sign-On Rule for the Default Policy
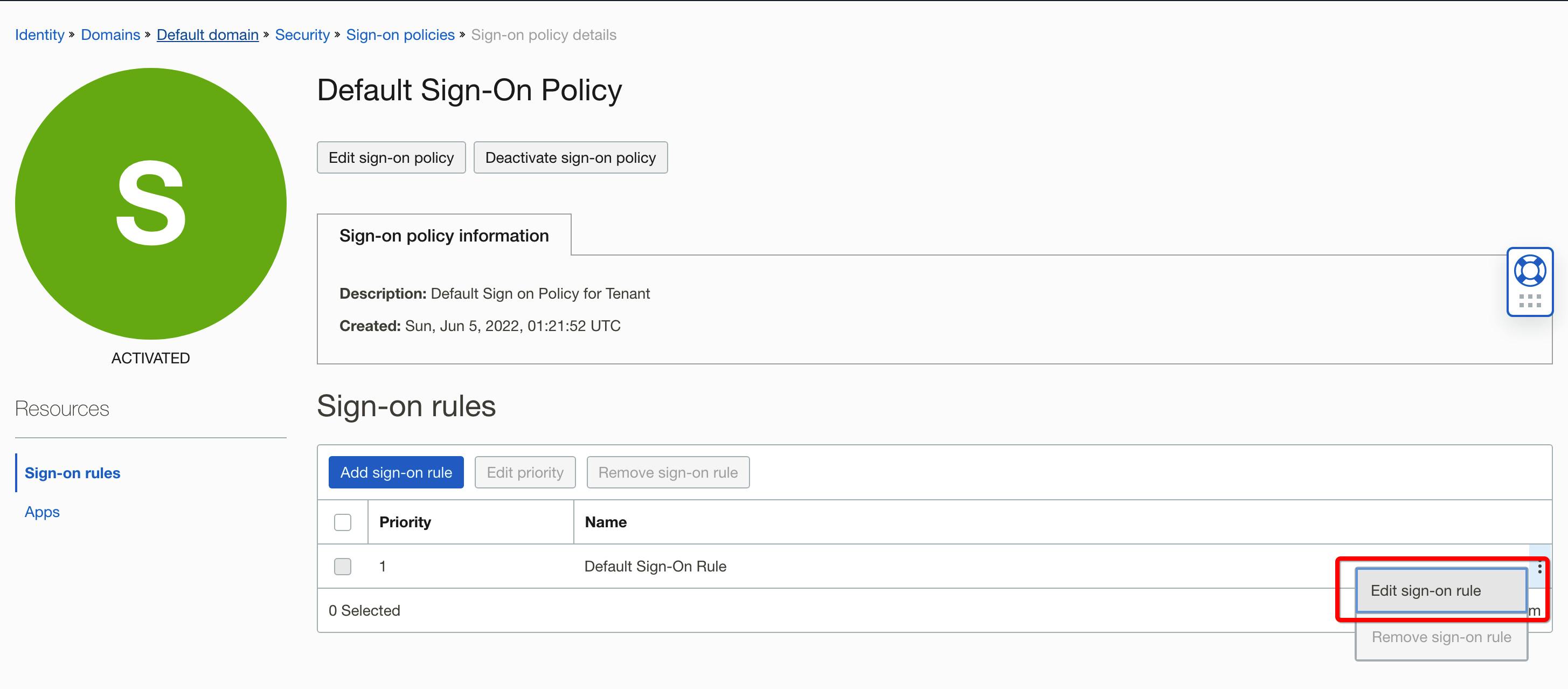
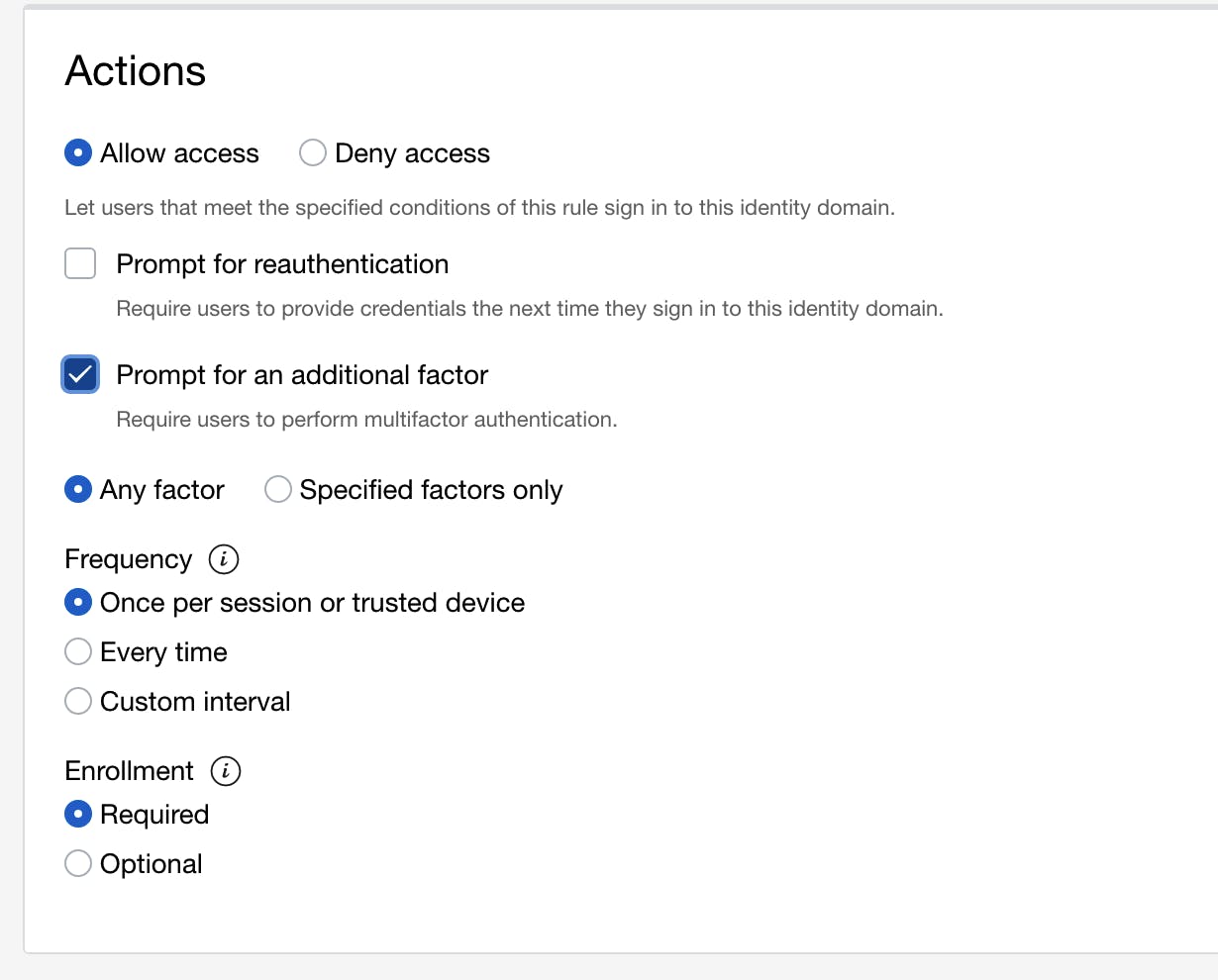
Sign-on Rules are evaluated one at a time in order. Update the actions for the default rule and save. Do not log out of this window until you have verified you can still log in.
Test
Log into OCI using an Incognito window. OCI will now prompt you to setup additional factors:
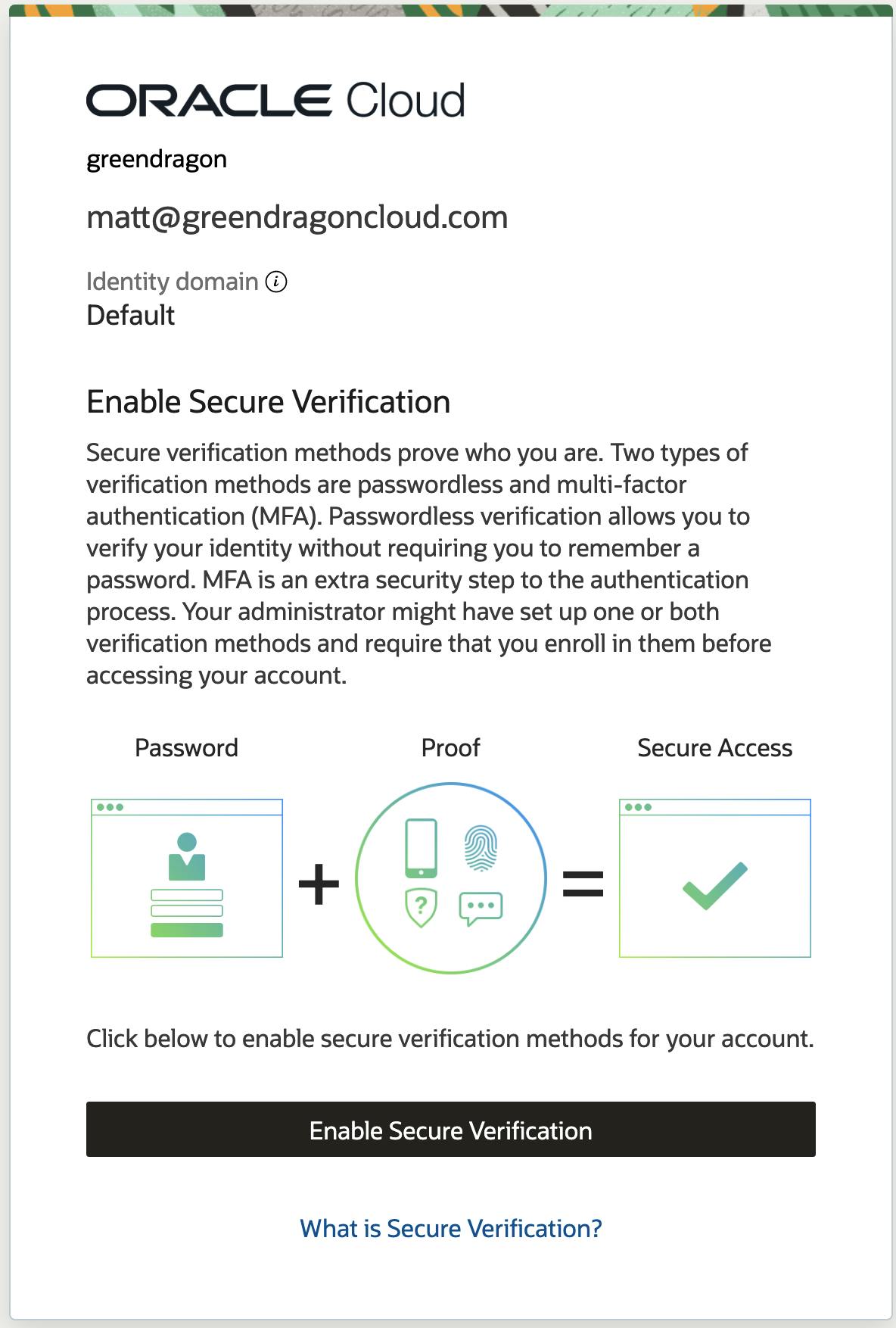
Download the Oracle app to your phone and scan the QR code:
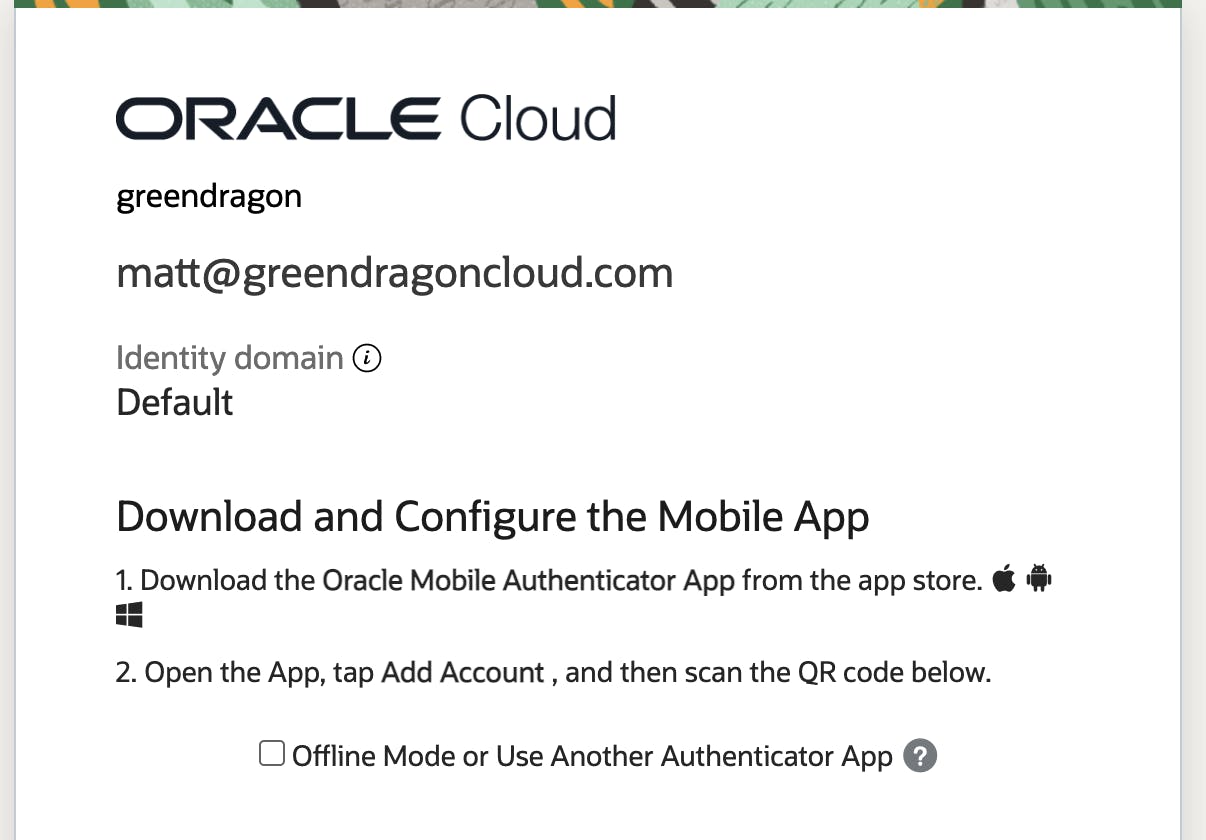
Note, you can also use Google or Microsoft Authenticator.
Open a new Incognito Window and check your signon works.
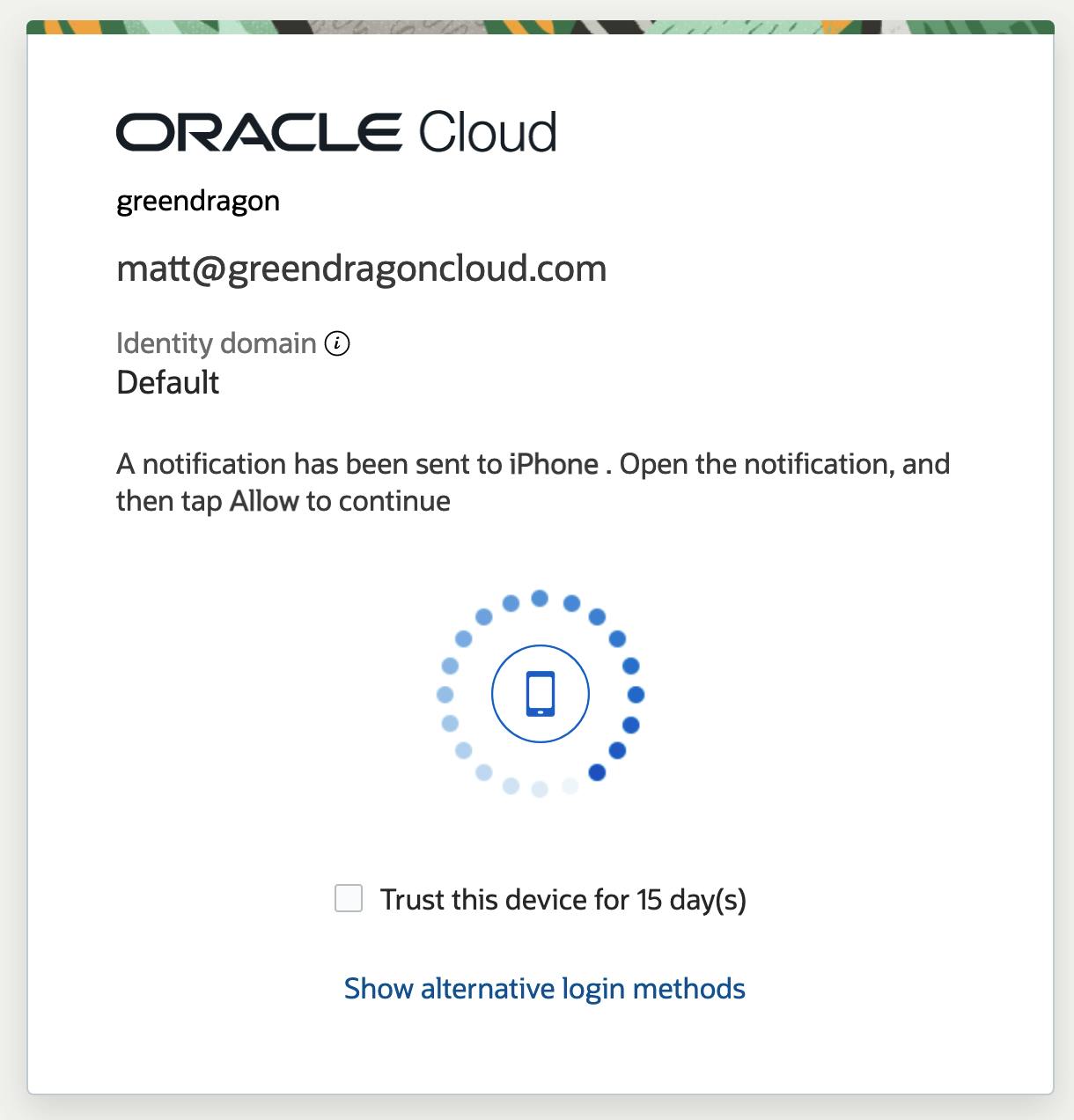
Once this has been verified, you're good to go. For additional security, add a network perimeter.
Adding a Network Perimeter
Network Perimeter
If you or your VPN has a static IP address, you can configure OCI to reject all connections from unknown IP addresses. While that may sound desirable, there's a significant risk you'd get logged out if your static IP address changes or you change your IP provider.
So I don't suggest you do this - a better configuration is for OIC to require MFA via the mobile app every time someone signs in outside the network perimeter.
Navigate back to Security then click on Network Perimeters.
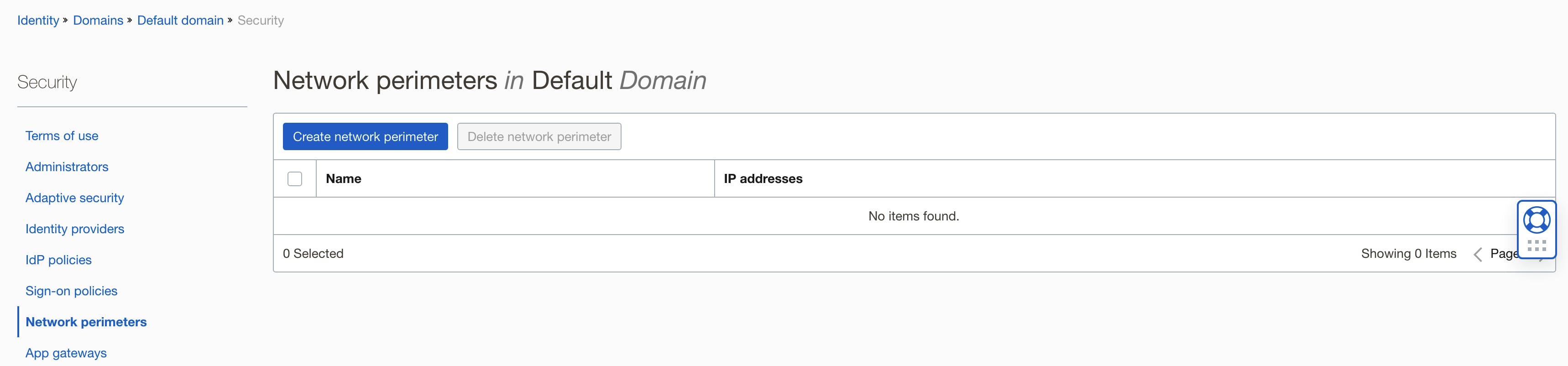
Add a Network Perimeter. CIDR can be used here, and you can establish your own IP address using a site such as https://www.iplocation.net
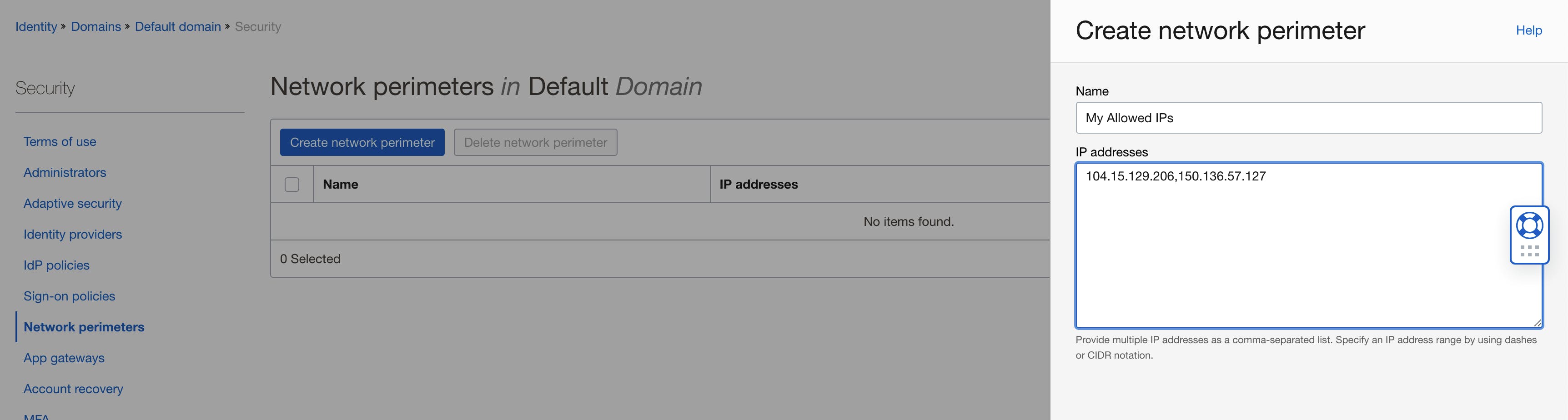
Sign-on Policy
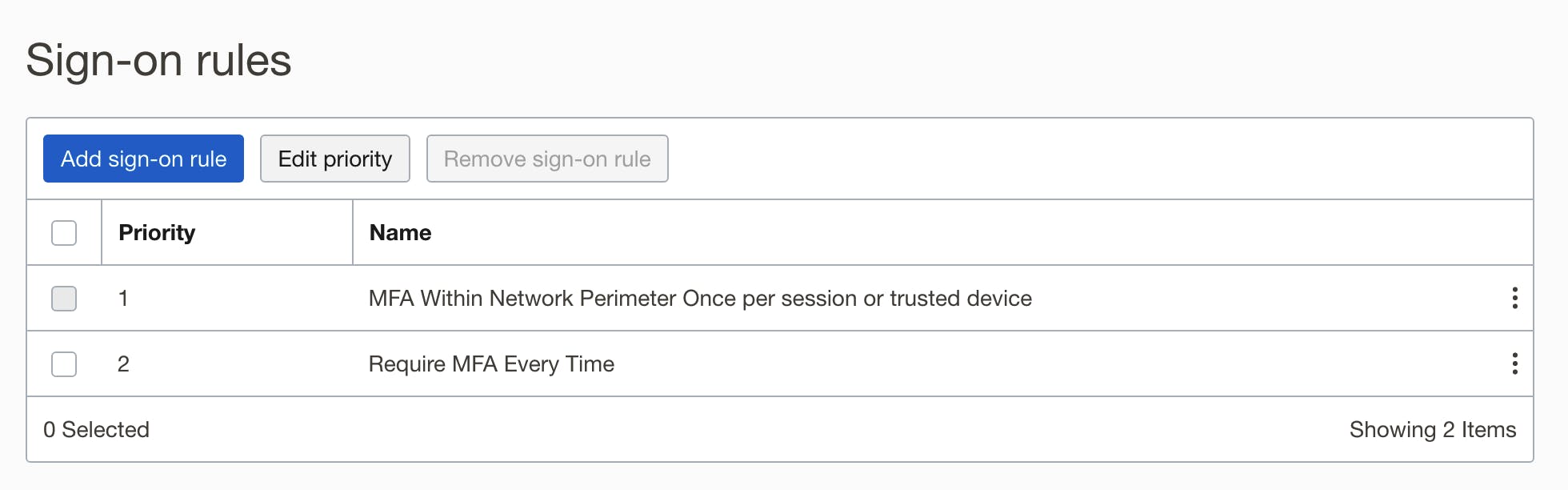
The rules will be amended as follows:
- The first rule will check to see if the user is within the Network Perimeter, in which case MFA is required with a frequency of "Once per session or trusted device", using any method (app, email etc).
- The second rule will apply when the above rule doesn't, i.e. when the user is outside of the Perimeter - it will require MFA with a frequency of "Every time", via the Mobile Authenticator app.
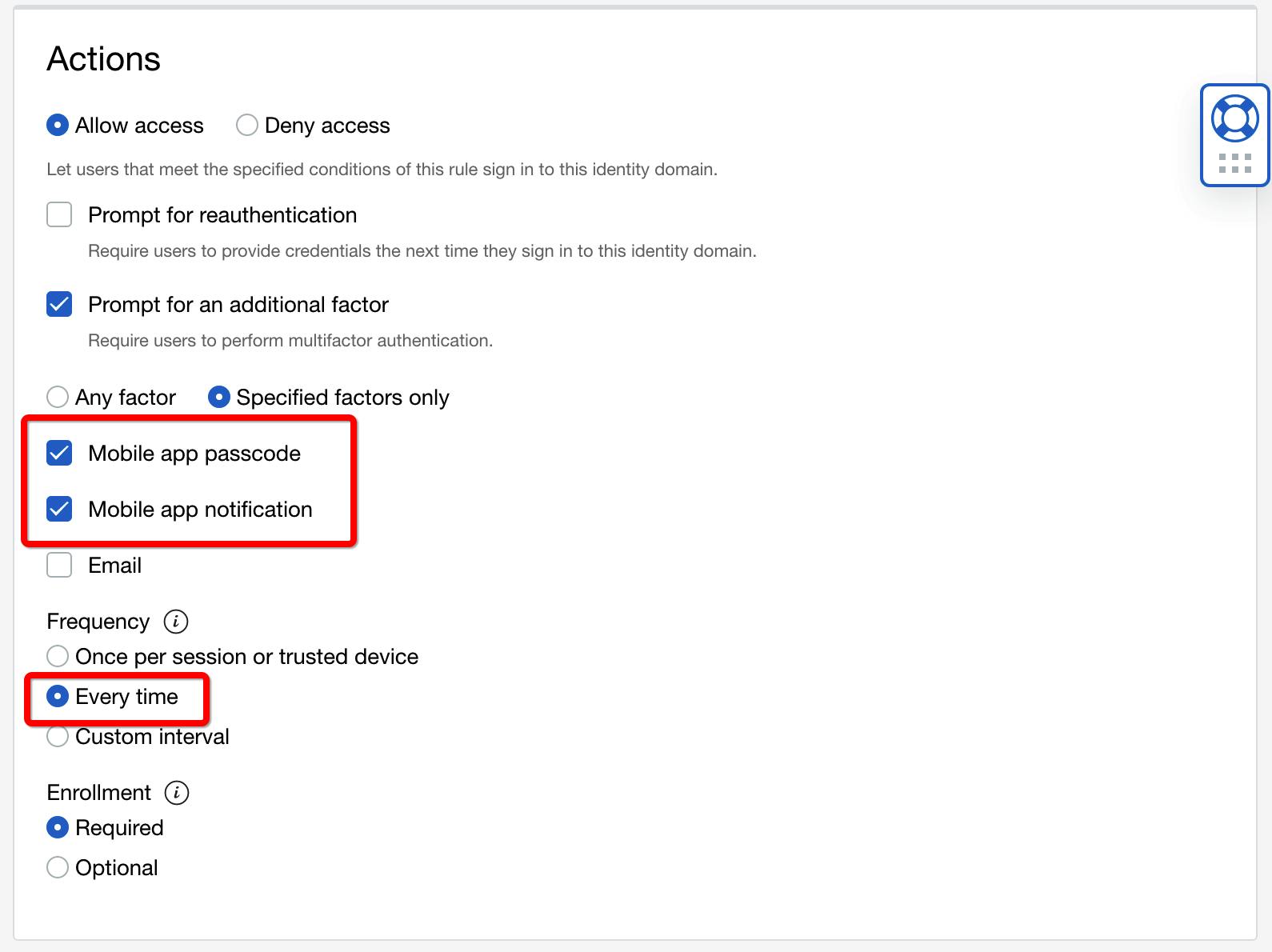
Test
Using Incognito browser windows or an alternate browser, verify successful signon and MFA behavior inside and outside the network perimeter. Sign out from your configuration session only when successful login has been verified.
Summary
Sign-on policies can be extended to meet your requirements - for example to include rules around Identity Providers and for use with specific apps, including APEX.
The basics shown in this article will help keep intruders out while you work out your security posture.
Now that that's done - you're free to configure those Always Free services and start to build great applications using APEX and Compute.